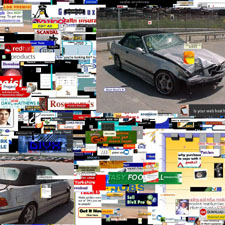
Blackhat & Defcon Collages
For my day job, I work in the information security field. You know, securing computer systems, and also trying to break into them. Its fun. Every year there are two conferences that cater to IT security people. They are Blackhat and Defcon. Blackhat is a corporate sponsored event and usually has some interesting talks and is populated with mostly corporate-types. Defcon on the other hand is supposed to be an ‘underground information security gathering’ event. However, since both conferences take place in the same place and at the same time, most of the Blackhat attendees also go to Defcon.


Anyway, since these two conferences a full of information security people, Internet access is a must. Therefore, both Blackhat and Defcon offer 802.11b wireless networks for the attendees to use while the conferences are going on. Given that an 802.11b network is a shared-media network (much like a single Ethernet segment), if you are connected to the network, you can sniff other people’s network traffic. Having a computer attached to either the Blackhat or Defcon wireless network is kinda like living in the wild wild west. Your computer will be attacked (repeatedly), the network may disappear, performance may suck, and your connections may be interrupted at any point. However, some people manage to at least do some web surfing while connected to these networks. At the conferences, there were plenty of people who wanted to disrupt the wireless networks. I wanted to have some fun with the networks, but I wanted to do something that was both non-obtrusive and semi- constructive. So, I figured it would be fun to try to capture all of the images from people’s web page requests (or other protocols) and make some type of artsy collage out of them.
After I had decided what I wanted to do, it was time to try to figure out how to make it happen. Unfortunately, I only had my little (underpowered) Toshiba Libretto with me running Windows XP while I was at the conferences. I’ve got Linux installed on it, but the PCMCIA slot doesn’t work right so I couldn’t use my wireless network card, and it really needs ACPI support (which doesn’t really work in the kernel yet), blah blah blah, etc. Therefore, I had to improvise a bit. After doing a little research, I came across a couple of programs that were designed to do exactly what I wanted! They were EtherPEG and Driftnet. EtherPEG wasn’t going to work because it a Macintosh-only program. Oh well. I then looked at Driftnet, but found out that it is Linux only. However, it looked like it could be adapted for my purposes. Although Driftnet has support for a GUI displaying images as they are captured, I was actually interested in running a program in the background and just capturing images to disk.
Since I had Cygwin installed on my laptop, I had some tools to work with. Also, I had WinPcap installed, which provided me with a pcap compatible sniffing library. So, I proceeded to downloaded the Driftnet source code and started hacking away. I ripped out all of the GUI support, tweaked a lot of files to fix variable type mismatches, and linked the program with WinPcap. Amazingly, after a hour of hacking or so, I had something up and running! So, by the second day of Blackhat, I was able to start capturing images.
For the last day of Blackhat and during the first day of Defcon, I fired up the modified Driftnet whenever I had a chance and grabbed images. When I got back from the conferences, I started analyzing the raw data I had collected. While casually browsing through the images, I found that there were some duplicates. Well, I suppose that was to be expected — Driftnet was just grabbing everything. So, I wrote a little Perl script that weeded out the dups. After that was done, I calculated the final statistics for what I had captured:
Blackhat - 2788 images, 5693k of data
Defcon - 8988 images, 27368k of data
My next challenge was to generate a cool image collage out of this raw data. I’m a big fan of Jamie Zawinski‘s webcollage program. In fact, I have it running on a system at home all the time. It generates great web collages, but it normally does this by making requests to random web pages for its source material. A recent version introduced support for Driftnet. However, it assumes that Driftnet would be run interactively. For me, this wasn’t the case — I just had a huge directory full of images. So, I did some more hacking and changed the code a bit so that it would just generate an image from my previously collected raw data. I set webcollage to generate some huge pictures (2048x2048) for both the Blackhat and Defcon data sets. It took a while to churn through the data, but eventually it spit out a couple of really cool iamges. Below are the results. Each image has been broken down into four quadrants to be a little easier to manage.
Blackhat
DefCon
Blackhat: 2048x2048 JPEG image (1109k). Raw data zip file (6034k).
Defcon: 2048x2048 JPEG image (1113k). Raw data zip file (26477k).